Walmart Embraces Amazon MCF: A New Era of Cross-Platform Fulfillment for eCommerce
Walmart Embraces Amazon MCF: A New Era of Cross-Platform Fulfillment for eCommerce
M-commerce is getting popular every day, especially after the covid outbreak. The trend for mobile commerce and mobile devices has increased drastically. This mobile revolution has changed every aspect of our daily lives, i.e., how we shop, study or work. Mobile has made everything easier, quicker, and more efficient. Loads of advantages attracted many businesses and shoppers towards the use of it. But the thing most mobile users are concerned about is mobile app security. Mobile apps are convenient, fast, and efficient. But one must carefully select and pick an app. About 60% of digital fraud is done on mobile, from stolen passwords to phishing attacks.
There are mobile apps available for almost everything, i.e., shopping, social media, bank transactions, etc. Moreover, apps also help businesses gather helpful information like usage statistics, users’ locations, likes, dislikes, and many more. These metrics help users to improve their services. And if any of these pieces of information fall into the wrong hands, it can be harmful to users, making mobile app security inevitable.
Mobile app security is securing apps from external threats like viruses and other cyber threats. These viruses and cyber threats may risk financial and other critical data from hackers.
Security of mobile applications has become parallelly crucial in today’s digital environment. A Mobile security breach can give hackers access to users’ personal information. Also give them other critical information like banking information, current location, and lots more.
Turn Your Online Store Into a Fast, Fascinating, And Secure Mobile Application
Users usually rely on the app development firms to check and ensure the security of their applications before the final launch. However, below are some facts and stats discovered in study research by IBM.

So the above facts and stats are enough to comprehend that most application development firms do not take much stress on ensuring the security of the mobile apps. And taking advantage of these loopholes, hackers can misuse any of the following things.
Hackers can steal the user’s financial data like credit card or debit numbers and perform transactions. Recent research from Kaspersky discovered a banking trojan called ‘Gimp. Utilizing this trojan, hackers use the information of covid infected people to convince Android users to give away their credit card information. Gimp has a special interface that shows the number of infected people near you and convinces you to pay money to see the number of infected people near you. Anubis trojan is a similar malicious software categorized as a banking trojan. So this malware gathers valuable financial data from users’ devices.
This way hackers steal the financial information of the user and can make illegal transactions from his card.
Read Also: What are the top mobile Commerce trends that will dominate 2024?
Apart from financial data, hackers can breach numerous other critical data, like any user’s account or website credentials. A similar type of malware enters the user’s device via downloaded apps. It can infect the device, force it to send or receive messages, request permission to access the device location. Moreover, it can also read the contact list, allow push notifications. And do anything harmful without your permission.
Hackers can illegally access the premium version or special features of the app. This can cause a revenue loss. This type of hacking is especially done in utility and gaming apps. Where the premium features are the major source of income.
Though there are many security threats to mobile apps that can breach their data financially. And give it a financial loss, there are still certain crucial steps to prevent it.
Any mobile app developed for any business may contain some important digital assets. Any security infringement on the app can put the entire business in jeopardy. Top-quality app development firms strive every moment to ensure the security of the app. They perform Security risk analysis in the following ways.
Apps with permeable firewalls are at consistent risk of being infringed by hackers. So these hackers can illegally access important data like PINs, system passwords, payment credentials, etc.
All the apps must be functioning under the legal framework.
Permission gives the user the access to utilize more features. But also permissions make apps vulnerable to hackers. The app should not allow permissions beyond the functional area of any app. And developers should avoid recycling the existing libraries. But create new ones that selectively seek permissions.
Most apps ask users to save the passwords to save them from entering credentials each time they log in. Saving password to the mobile device is insecure and can be misused in the case of mobile theft. To avoid this, users must save their passwords on the app server instead of on the device. So saving passwords to the app server lets users change passwords in case of mobile theft.
Confidential information stored in the app without proper protection is prone to cyber-attacks. Miscreants can acquire confidential data by reverse engineering techniques. So it is imperative to store as fewer data as possible to minimize the risk.
It is usually observed that users normally forget to log out app or website after using it. This can be very harmful in most cases. And to avoid this, enforce session logout is done. In enforce, session logout users are automatically logging out of the app. After a certain time of inactivity to ensure security. So enforcing session logout is important to log out after a certain period of inactivity.
Penetration testing is done to discover the known weaknesses in an app. It aims to discover potential shortcomings that a hacker could utilize to breach the app’s security. Also includes checking unencrypted data, weak password policy, authorizations to third-party apps, etc. So regularly performing penetration testing is good for the security of your app. Black and White box testing are different kinds of penetration testing measures.
In this world of digitization, mobile apps have become necessary for different purposes. These applications have made daily life tasks much easier, but at the same time, they can be harmful if not used carefully. If you are planning to create an app for your online store, you must ensure its security. So get your app developed by a reliable and experienced mobile app development company.

Walmart Embraces Amazon MCF: A New Era of Cross-Platform Fulfillment for eCommerce
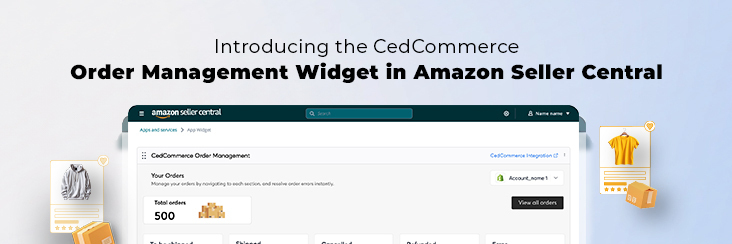
Order Management Redefined: A Centralized Solution for Amazon Sellers

Maximizing TikTok Shop’s Regional Compatibility for US, UK, and EU Markets

Understanding U.S. Tariffs in 2025: What Sellers Need to Know and Do

Walmart’s Search Algorithm Decoded: How to Rank Higher & Sell More

TikTok Gets a 75-Day Reprieve in the USA as Trump Signals Hope for a Deal

TikTok Shop Introduces Category-Based Benchmarks for Product Listings – What Sellers Need to Know

Amazon FBA vs. FBM: Which Fulfillment Method Is Right for You?

Amazon Launches Another AI Tool for Sellers: AI Generated Product Enrichment

Top 10 Selling Items on eBay in 2025
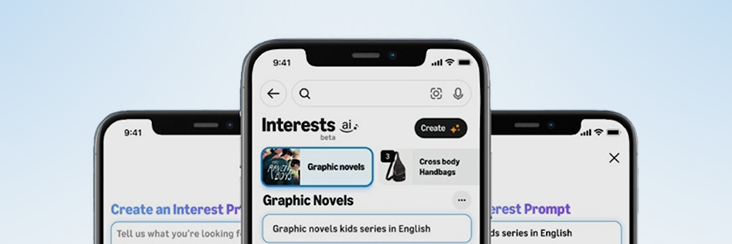
Amazon launches AI Powered ‘Interests’ Feature to Improve Shopping Experience
Is TikTok Staying in the US? The State of TikTok Ban

Best Buy coming back to the US, Marketplace Relaunch and New Opportunities in Store!

Miravia PrestaShop Connector: Built for Smart Sellers

Walmart Launches “Wally”, AI Assistant For Merchants

TikTok Shop to Start Business in Germany, France, and Italy

TikTok Shop Surges as Americans Spend $700 Annually, Defying Regulatory Pressures

Amazon’s Longest Prime Day Ever: What You Need to Know

eCommerce Growth in the Netherlands: A 5% Surge in 2024 with Bright Prospects Ahead

CedCommerce Launches Shopee & Lazada Integration for WooCommerce on WordPress.com